AI Risk Management Framework: A Technical Deep Dive for AI Developers
AI Risk Management Framework guides developers to build AI systems by identifying and mitigating risks through testing, secure coding, and continuous monitoring.
Join the DZone community and get the full member experience.
Join For FreeThe rapid integration of artificial intelligence (AI) into software systems brings unprecedented opportunities and challenges for the software development community. As developers, we're not only responsible for building functional AI systems, but also for ensuring they operate safely, ethically, and responsibly. This article delves into the technical details of the NIST AI Risk Management Framework, providing concrete guidance for software developers building and deploying AI solutions.
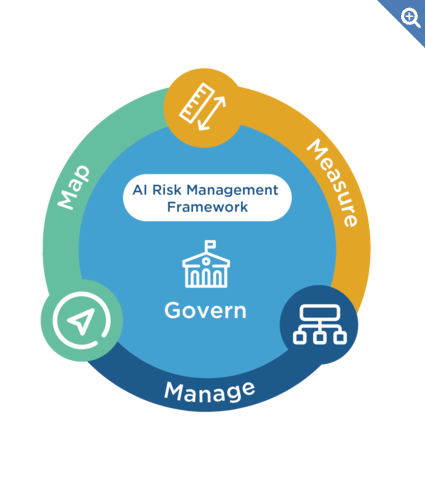
Image from NIST webpage
The NIST framework lays out 4 important steps for AI developers to adopt to reduce the risk associated with AI.
1. Govern: Setting up the Fundamentals
Governance is the most important and the foundation for this framework. Effective governance of AI risk starts with solid technical groundwork. In order to implement robust governance, developers of AI systems should explore some of the following approaches
- Version control and reproducibility: Implement rigorous version control for datasets, model architectures, training scripts, and configuration parameters. This ensures reproducibility, enabling tracking of changes, debugging issues, and auditing model behavior.
- Documentation and code review: Establish clear documentation requirements for all aspects of AI development. Conduct thorough code reviews to identify potential vulnerabilities, enforce coding best practices, and ensure adherence to established standards.
- Testing and validation frameworks: Build comprehensive testing frameworks to validate data quality, model performance, and system robustness. Employ unit tests, integration tests, and regression tests to catch errors early in the development cycle.
Table 1: Examples of Technical Governance Approaches
|
Aspect |
Approach |
Example |
|
Version Control |
Utilize Git for tracking code, data, and model versions. |
Document commit messages with specific changes, link to relevant issue trackers. |
|
Documentation |
Use Sphinx or MkDocs to generate documentation from code comments and Markdown files. |
Include API references, tutorials, and explanations of design decisions. |
|
Testing |
Employ frameworks like Pytest or JUnit for automated testing. |
Write tests for data loading, model training, prediction accuracy, and security vulnerabilities. |
2. Map: Identifying Technical Risks in AI Systems
Understanding the technical nuances of AI systems is crucial for identifying potential risks. Some of the key areas to explore for mapping the AI risks are:
- Data quality and bias: Assess the quality and representativeness of training data. Identify potential biases stemming from data collection, labeling, or sampling methodologies. Implement data pre-processing techniques (e.g., outlier detection, data cleaning) to mitigate data quality issues.
- Model robustness and adversarial attacks: Evaluate the vulnerability of AI models to adversarial examples – inputs designed to mislead the model. Implement adversarial training techniques to enhance model robustness and resilience against malicious inputs.
- Security vulnerabilities: Analyze the software architecture for security flaws. Implement secure coding practices to prevent common vulnerabilities like SQL injection, cross-site scripting, and authentication bypass. Employ penetration testing and vulnerability scanning tools to identify and address security weaknesses.
Table 2: Examples of Technical Risk Identification
|
Risk Category |
Description |
Example |
|
Data Bias |
Training data reflects historical or societal biases. |
An AI-powered credit card approval trained on data with historical bias against certain demographic groups might unfairly deny credit cards to individuals from those groups. |
|
Adversarial Attacks |
Maliciously crafted inputs designed to fool the model. |
An image recognition system could be tricked by an adversarial image to misclassify a positive as a negative result. |
|
Data Poisoning |
Injecting malicious data into the training dataset to compromise model performance. |
An attacker could insert corrupted data into a spam detection system's training set, causing it to misclassify spam messages as legitimate. |
3. Measure: Evaluating and Measuring Technical Risks
Evaluating the technical severity of risks requires quantitative metrics and rigorous analysis. A few metrics that we could deploy to measure the performance of AI include,
- Model performance metrics: Utilize relevant performance metrics to assess model accuracy, precision, recall, and F1 score. Monitor these metrics over time to detect performance degradation and identify potential retraining needs.
- Explainability and interpretability: Implement techniques like LIME (Local Interpretable Model-agnostic Explanations) or SHAP (SHapley Additive exPlanations) to understand model decision-making processes. Utilize visualization tools to interpret model behavior and identify potential biases.
- Security assessment tools: Employ static code analysis tools to identify security flaws in the source code. Use dynamic analysis tools (e.g., fuzzing, penetration testing) to uncover vulnerabilities in running systems.
Table 3: Technical Risk Measurement Techniques
|
Technique |
Description |
Example |
|
Confusion Matrix |
Visualizes the performance of a classification model by showing true positives, true negatives, false positives, and false negatives. |
Analyzing a confusion matrix can reveal if a model is consistently misclassifying certain categories, indicating potential bias. |
|
LIME |
Generates local explanations for model predictions by perturbing input features and observing the impact on the output. |
Using LIME, you can understand which features were most influential in a specific loan denial decision made by an AI model. |
|
Penetration Testing |
Simulates real-world attacks to identify security vulnerabilities in a system. |
A penetration test could uncover SQL injection vulnerabilities in an AI-powered chatbot, enabling attackers to steal user data. |
4. Manage: Implementing Risk Controls
Managing technical risks demands the implementation of robust controls and mitigation strategies. Some of the strategies to explore for managing the technical risks are
- Data de-biasing techniques: Implement techniques like re-weighting, data augmentation, or adversarial de-biasing to address biases in training data. if possible conduct fairness audits using appropriate metrics to evaluate the fairness of model outcomes.
- Secure software development practices: Adhere to secure coding principles to minimize security vulnerabilities. Use strong authentication mechanisms, encrypt sensitive data, and implement access control measures to safeguard systems and data.
- Model monitoring and anomaly detection: Establish continuous monitoring systems to track model performance and detect anomalies. Implement techniques like statistical process control or machine learning-based anomaly detection to identify deviations from expected behavior.
Table 4: Technical Risk Mitigation Strategies
|
Risk |
Mitigation Strategy |
Example |
|
Data Bias |
Data Augmentation: Generate synthetic data to increase the representation of underrepresented groups. |
Augment a dataset for facial recognition with synthetic images of individuals from diverse ethnic backgrounds to reduce bias. |
|
Adversarial Attacks |
Adversarial Training: Train the model on adversarial examples to improve its robustness against such attacks. |
Use adversarial training to improve the resilience of an image classification model against attacks that aim to manipulate image pixels. |
|
Data Poisoning |
Data Sanitization: Implement rigorous data validation and cleaning processes to detect and remove malicious data. |
Employ anomaly detection algorithms to identify and remove outliers or malicious data points injected into a training dataset. |
Conclusion
As AI developers, we play a pivotal role in shaping the future of AI. By integrating the NIST AI Risk Management Framework into our development processes, we can build AI systems that are not only technically sound but also ethically responsible, socially beneficial, and worthy of public trust. This framework empowers us to address the technical complexities of AI risk, allowing us to create innovative solutions that benefit individuals, organizations, and society as a whole.
Opinions expressed by DZone contributors are their own.

Comments