Constructing Secure and Strong Data Access Layers With JPA
Determine how to control JPA features and secure coding practices to build secure data access layers that protect sensitive information in your applications.
Join the DZone community and get the full member experience.
Join For FreeData Security Is an Evolving Challenge With JPA
In the present era, where data drives everything, keeping sensitive information safe is more important than ever. As developers, we use JPA — Java Persistence API to work with relational databases, but we often overlook security aspects. Here, we will explore how to use JPA's features to create secure and reliable data access layers, protecting the integrity and confidentiality of your data.
The Security Threat Horizon
Data access layers are a major target for malicious actors. Common threats include:
Exploiting vulnerabilities in queries where user input is directly incorporated into SQL statements, Modifying sensitive data stored in your database, and bypassing authentication and authorization mechanisms to access data.
JPA Features for Secure Queries
While JPA doesn’t automatically make your application secure, it provides several features that can help reduce the risk of attacks:
By separating data from the actual SQL query, these statements eliminate the risk of SQL injection attacks, using placeholders for parameters within the query helps prevent SQL injection, this allows you to construct dynamic queries using criteria builders and predicates, keeping the query logic separate from the actual SQL string.
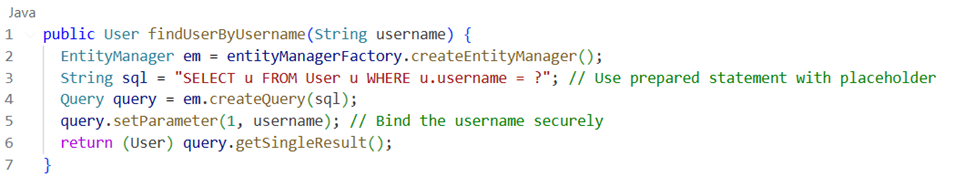
Secure Coding Practices With JPA
In addition to using JPA features, it's crucial to follow these secure coding practices:
Always validate user input before using it in JPA queries, implement strong authentication and authorization mechanisms, and encrypt sensitive data both when it's stored (at rest) and when it's being transmitted.
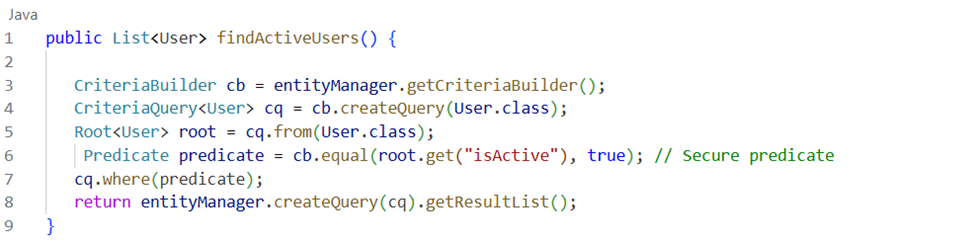
The above code demonstrates secure coding practices with JPA, such as using prepared statements and Criteria API
Understanding the Code
In the above example, the Java Persistence API securely retrieves user data. First, we obtain an instance of the entityManager, which serves as the central interface for interacting with JPA entities. This entity manager instance acts as a gateway for performing various JPA operations.
Next, we create a CriteriaBuilder object, which enables us to construct criteria queries dynamically. This approach allows for flexible and efficient querying.
Now let's focus on the crucial aspect of secure coding — defining the filtering condition for the query using a Predicate. In this case, we utilize the cb.equal method to create a predicate that checks if the "isActive" field of the user entity is equal to true. This ensures that only active users are retrieved, promoting data integrity and security.
Finally, we build the query string using a placeholder for the username. This approach separates the data (username) from the actual SQL statement, preventing potential security vulnerabilities like SQL injection attacks. By using parameterized queries, we can safeguard our application's database interactions.
Incorporate a Security-First Mindset
Building secure data access layers is an ongoing process. Additional tips include:
Staying updated with JPA libraries and frameworks, conducting regular security audits, and educating developers and stakeholders about data security best practices.
Workflow Wonders
JPA enables developers to build powerful and flexible data access layers. However, security is not a built-in guarantee. By using JPA's security features, observing secure coding practices, and maintaining a security-conscious approach, you can create robust data access layers that safeguard your valuable data and adopt trust in your applications.
Opinions expressed by DZone contributors are their own.

Comments